Development by Davis: “US Department of State unveils Open Book Project” plus 2 more |
- US Department of State unveils Open Book Project
- Security Enhancements in Jelly Bean
- AMD Wins Big at PR Daily's 2012 Digital PR and Social Media Awards
| US Department of State unveils Open Book Project Posted: 15 Feb 2013 12:00 AM PST  Earlier today, US Secretary of State Hillary Clinton unveiled the Open Book Project (remarks, project page, press notice), an initiative to expand access to free, high-quality educational materials in Arabic, with a particular focus on science and technolog |
| Security Enhancements in Jelly Bean Posted: 14 Feb 2013 08:59 PM PST Posted by Fred Chung, Android Developer Relations team Android 4.2, Jelly Bean, introduced quite a few new features, and under the covers it also added a number of security enhancements to ensure a more secure environment for users and developers. This post highlights a few of the security enhancements in Android 4.2 that are especially important for developers to be aware of and understand. Regardless whether you are targeting your app to devices running Jelly Bean or to earlier versions of Android, it's a good idea to validate these areas in order to make your app more secure and robust. Content Provider default access has changedContent providers are a facility to enable data sharing amongst app and system components. Access to content providers should always be based on the principle of least privilege — that is, only grant the minimal possible access for another component to carry out the necessary tasks. You can control access to your content providers through a combination of the In the example below, the provider <provider android:name="com.example.ReadOnlyDataContentProvider" android:authorities="com.example" android:exported="true" android:readPermission="com.example.permission.READ_DATA" /> Since the Prior to Jelly Bean, the default behavior of the <provider android:name="com.example.ReadOnlyDataContentProvider" android:authorities="com.example" /> Starting in Android 4.2, the default behavior for the same provider is now "not exported", which prevents the possibility of inadvertent data sharing when the attribute is not declared. If either the While this change helps to avoid inadvertent data sharing, it remains the best practice to always explicitly declare the New implementation of SecureRandomAndroid 4.2 includes a new default implementation of In general, the switch to the new A recommended approach is to generate a truly random AES key upon first launch and store that key in internal storage. Watch for details in a forthcoming post on Android cryptography. JavascriptInterface methods in WebViews must now be annotatedJavascript hosted in a On the one hand, this was a flexible mechanism; on the other hand, any untrusted content hosted in a WebView could potentially use reflection to figure out the public methods within the Beginning in Android 4.2, you will now have to explicitly annotate public methods with // Annotation is needed for SDK version 17 or above. @JavascriptInterface public void doSomething(String input) { . . . } Secure USB debuggingAndroid 4.2.2 introduces a new way of protecting your apps and data on compatible devices — secure USB debugging. When enabled on a device, secure debugging ensures that only host computers authorized by the user can access the internals of a USB-connected device using the ADB tool included in the Android SDK. Secure debugging is an extension of the ADB protocol that requires hosts to authenticate before accessing any ADB services or commands. At first launch, ADB generates an RSA key pair to uniquely identifies the host. Then, when you connect a device that requires secure debugging, the system displays an authorization dialog such as the one shown below. 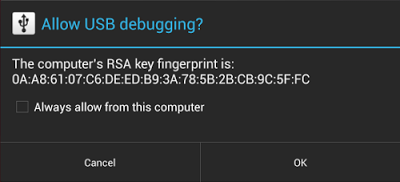 The user can allow USB debugging for the host for a single session or can give automatic access for all future sessions. Once a host is authorized, you can execute ADB commands for the device in the normal way. Until the device is authorized, it remains in "offline" state, as listed in the For developers, the change to USB debugging should be largely transparent. If you've updated your SDK environment to include ADB version 1.0.31 (available with SDK Platform-tools r16.0.1 and higher), all you need to do is connect and authorize your device(s). If your development device appears in "offline" state, you may need to update ADB. To so so, download the latest Platform Tools release through the SDK Manager. Secure USB debugging is enabled in the Android 4.2.2 update that is now rolling out to Nexus devices across the world. We expect many more devices to enable secure debugging in the months ahead. More information about security best practicesFor a full list of security best practices for Android apps, make sure to take a look at the Security Tips document. |
| AMD Wins Big at PR Daily's 2012 Digital PR and Social Media Awards Posted: 14 Feb 2013 12:00 AM PST Last month, AMD (NYSE: AMD) was awarded eight top honors at PR Daily's annual Digital PR and Social Media Awards, recognizing the company's marketing and communications teams for executing innovative programs to increase awareness for AMD solutions. The awards included 'Social M... |
| You are subscribed to email updates from Developers by Davis To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |


No hay comentarios:
Publicar un comentario